In today’s tutorial, we’ll see how to use KWalletManager to create a new wallet and use a GPG key for its encryption.
KWallet securely stores passwords and other sensitive information, allowing users to remember only a single password rather than numerous passwords and credentials.
Difficulty: ★☆☆☆☆
📜 Table of Contents
Using KGpg to create a GPG key
-
Start the KGpg program from the main menu. A dialog box appears, prompting us to select the GnuPG binary. We’ll use the system binary for this tutorial.
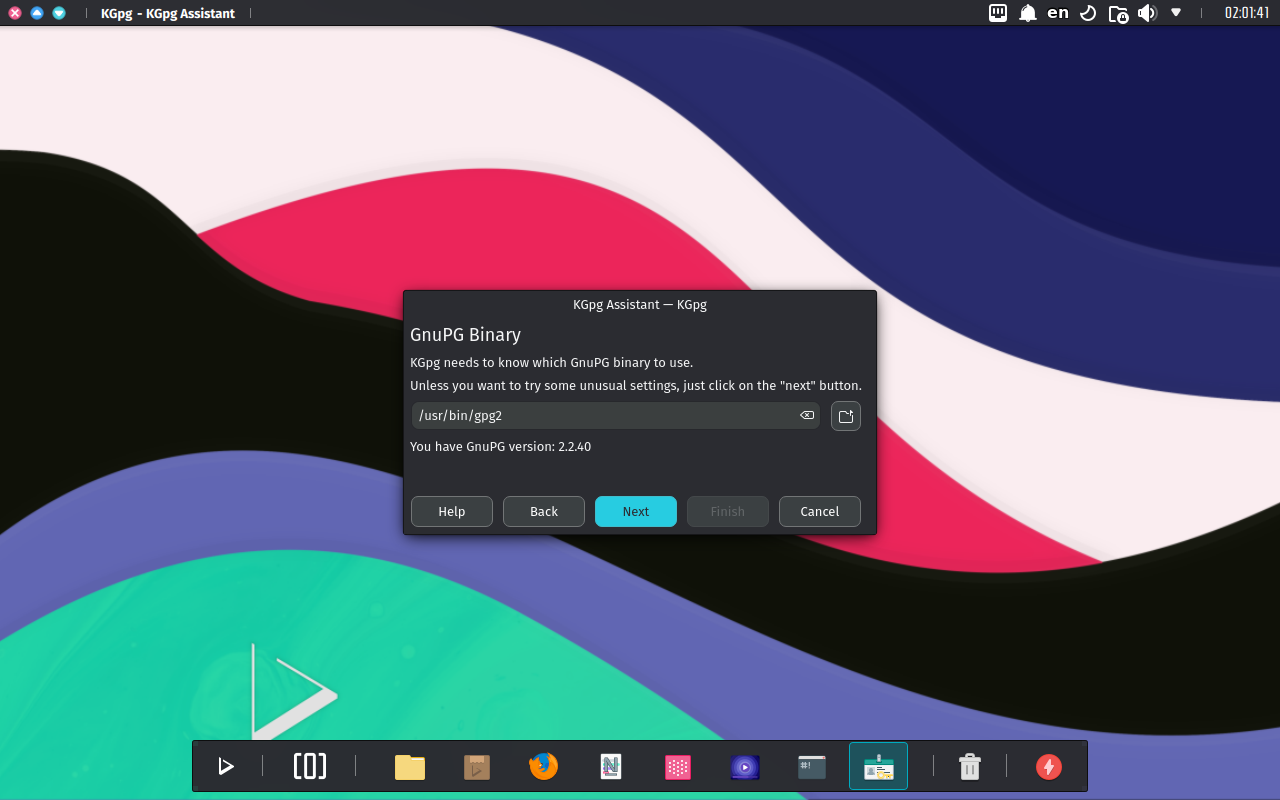
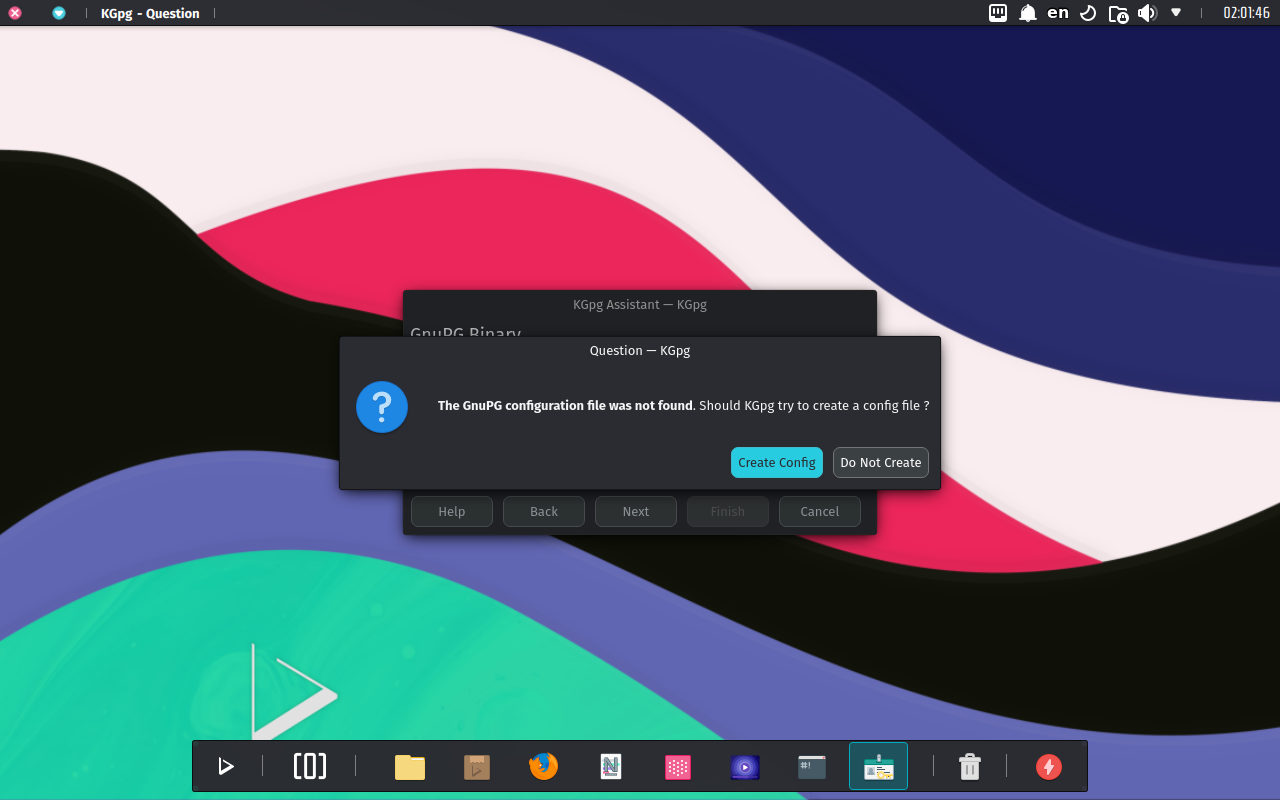
- If it can’t find one, KGpg will prompt us to create a GnuPG configuration file. Since this is a new key, we choose Create Config and leave the default file path.
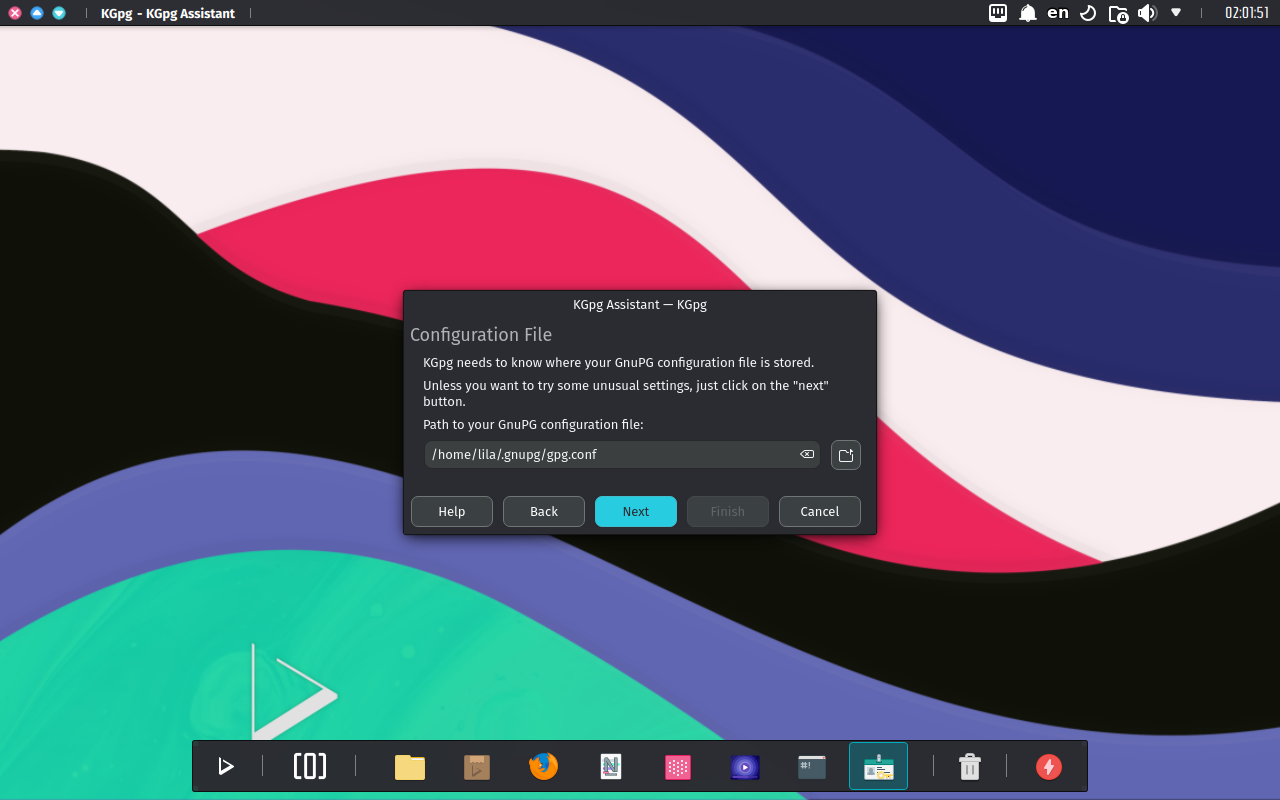
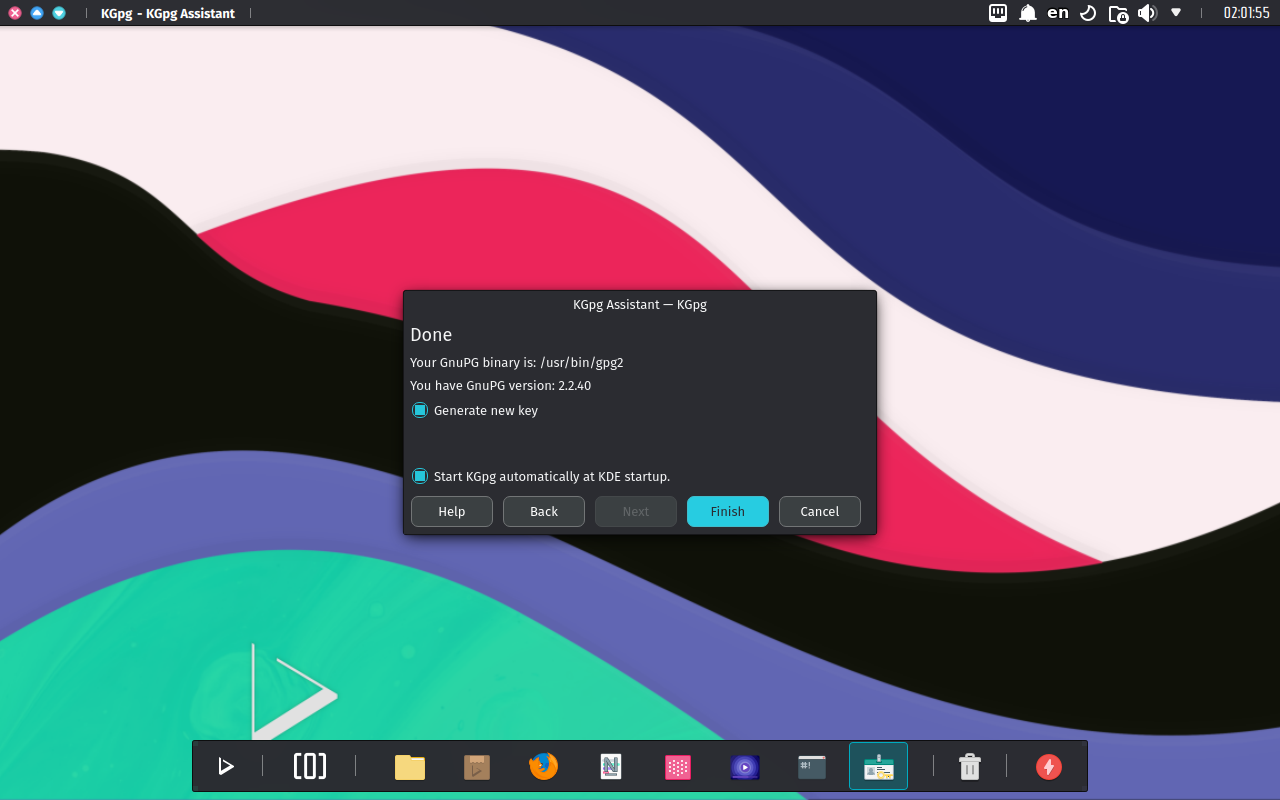
- Next, we click the Finish button to generate a new key.
- 🔰 Information: Generating a new key may take minutes, depending on the hardware.
-
A dialog box appears, prompting us to create a new key pair. Enter your name, email address, and an optional comment. We can also choose an expiration time for your key, the key strength (number of bits), and algorithms.
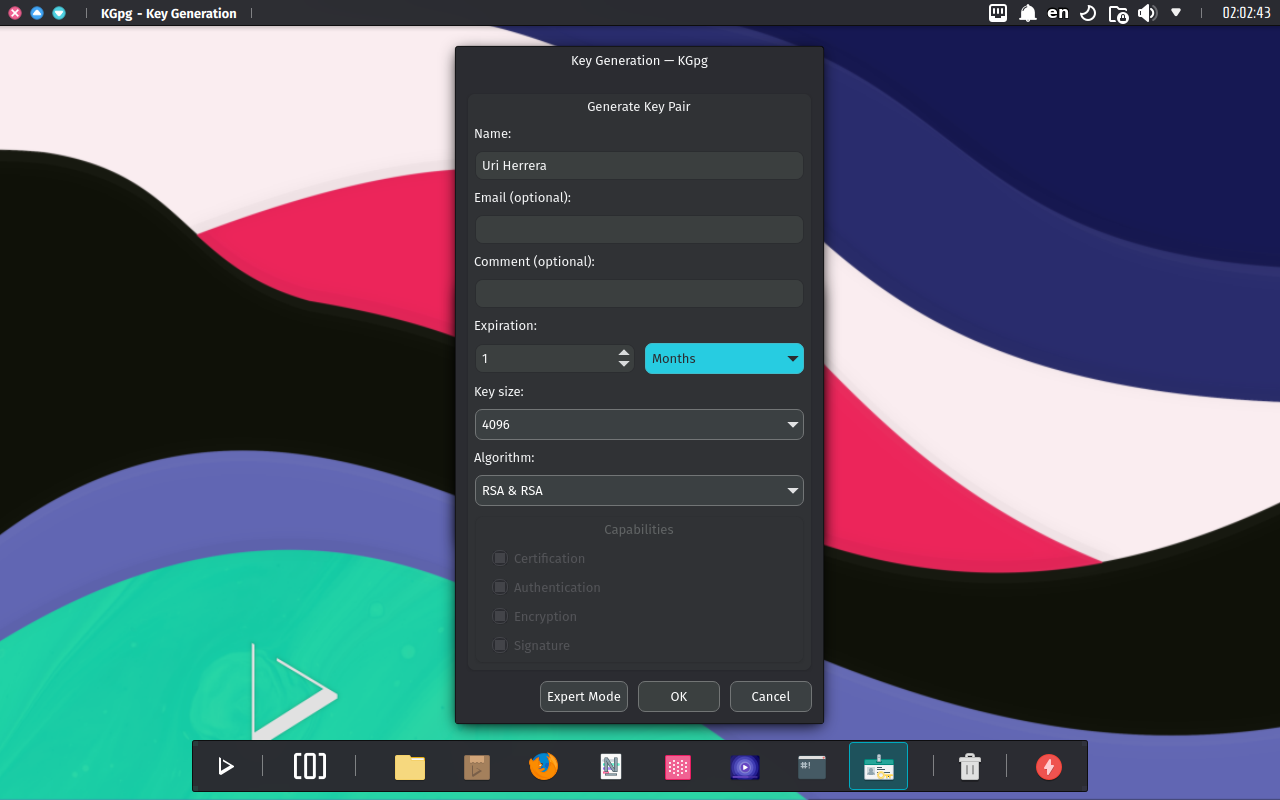
-
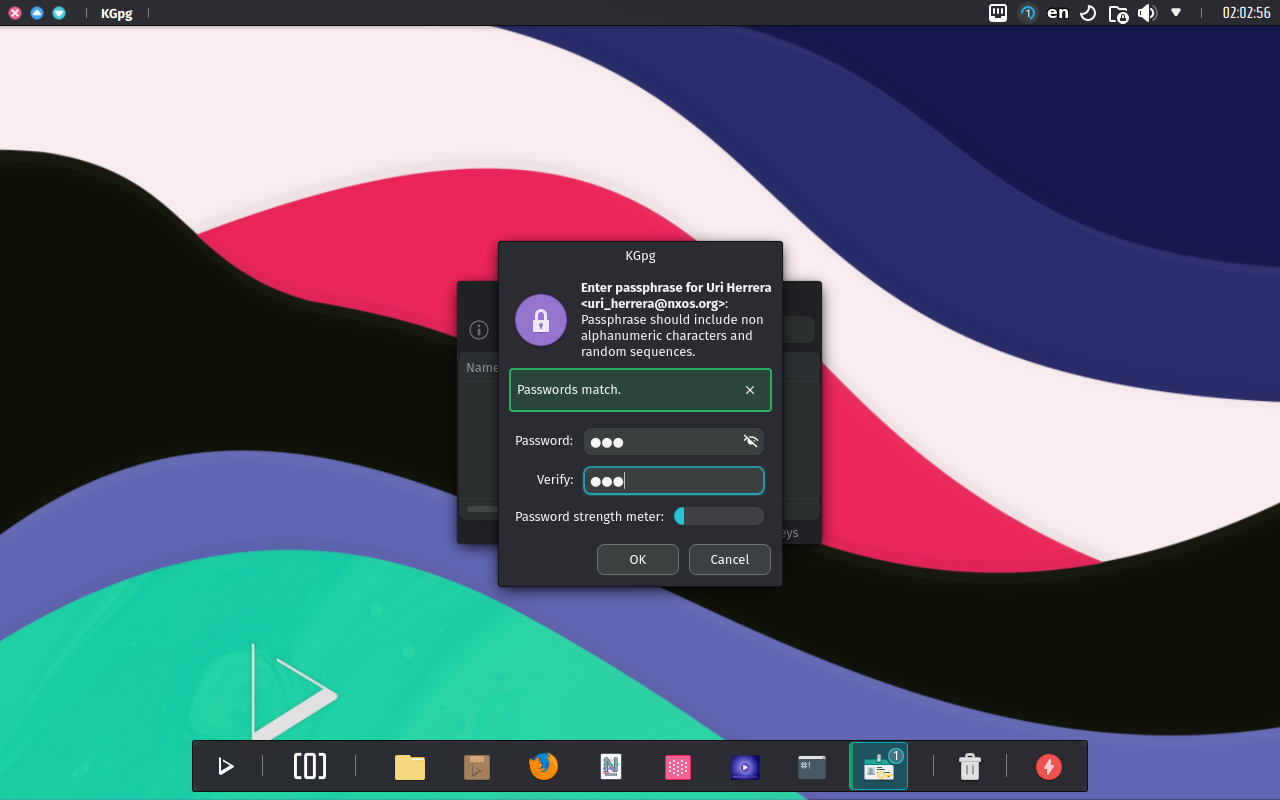
Enter the passphrase in the dialog box below. At this point, the key appears in the main KGpg window.
- ⚠️ Important: We won’t be able to decrypt the data if we forget the passphrase.
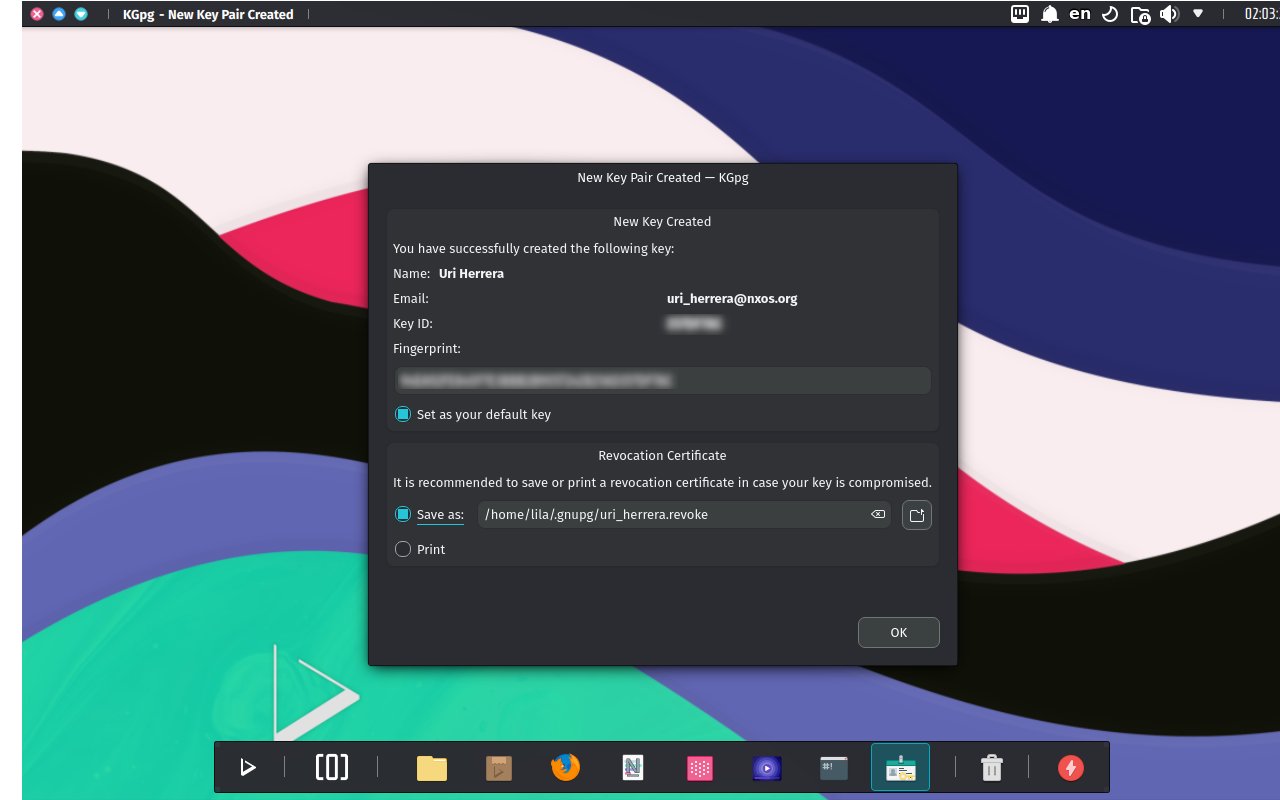
This GnuPG key will also be available in other keyrings, such as the GNOME Keyring. We also recommend adding this key when prompted.
Creating a new wallet using KDE Wallet KCM
By default, the wallet named kdewallet stores your passwords. Your login password secures this wallet, which will automatically open at login.
- To create a new wallet, open System Settings, navigate to the KDE Wallet KCM, enable the KDE Wallet subsystem, and click Apply. Then close and reopen System Settings.
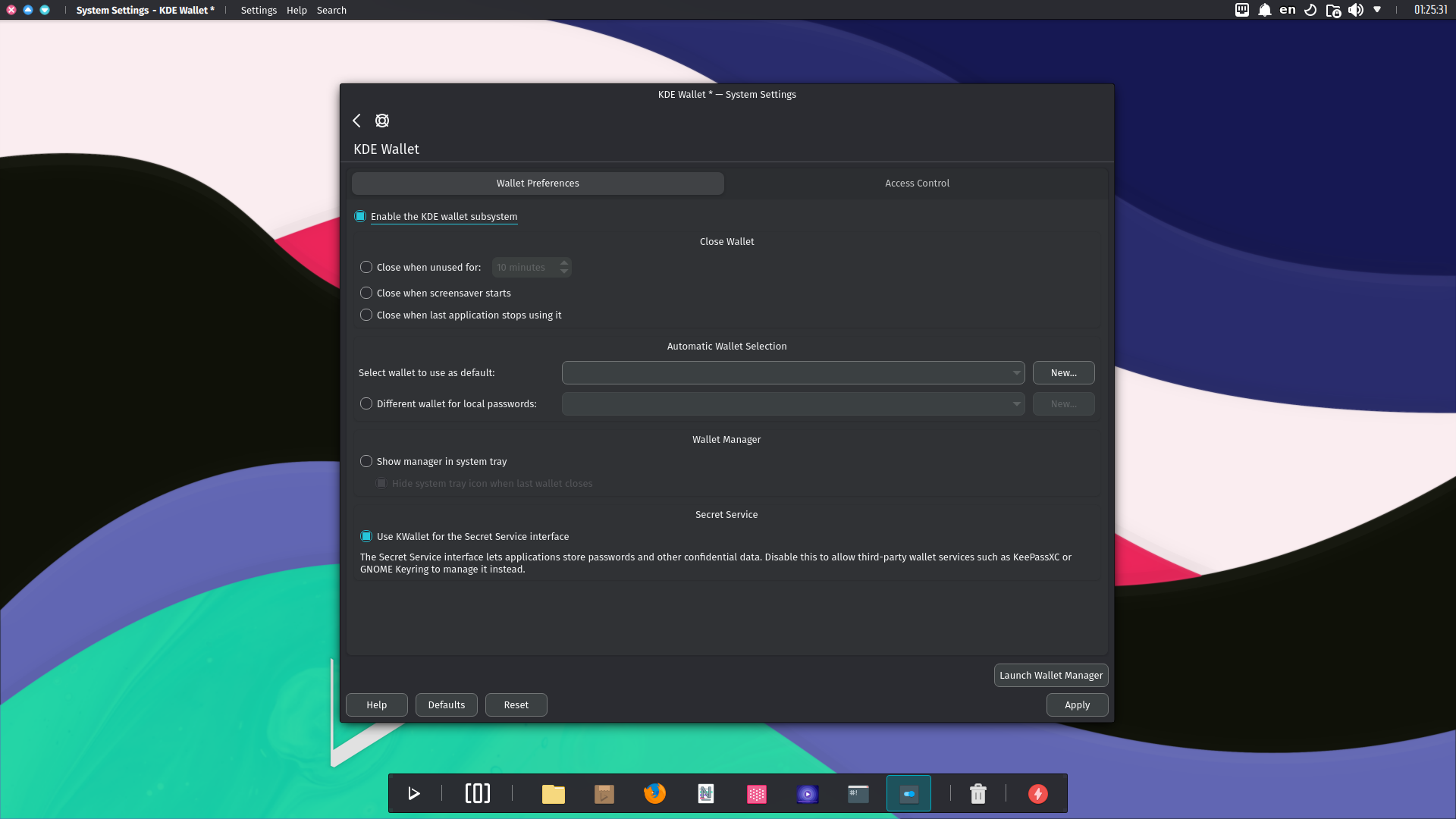
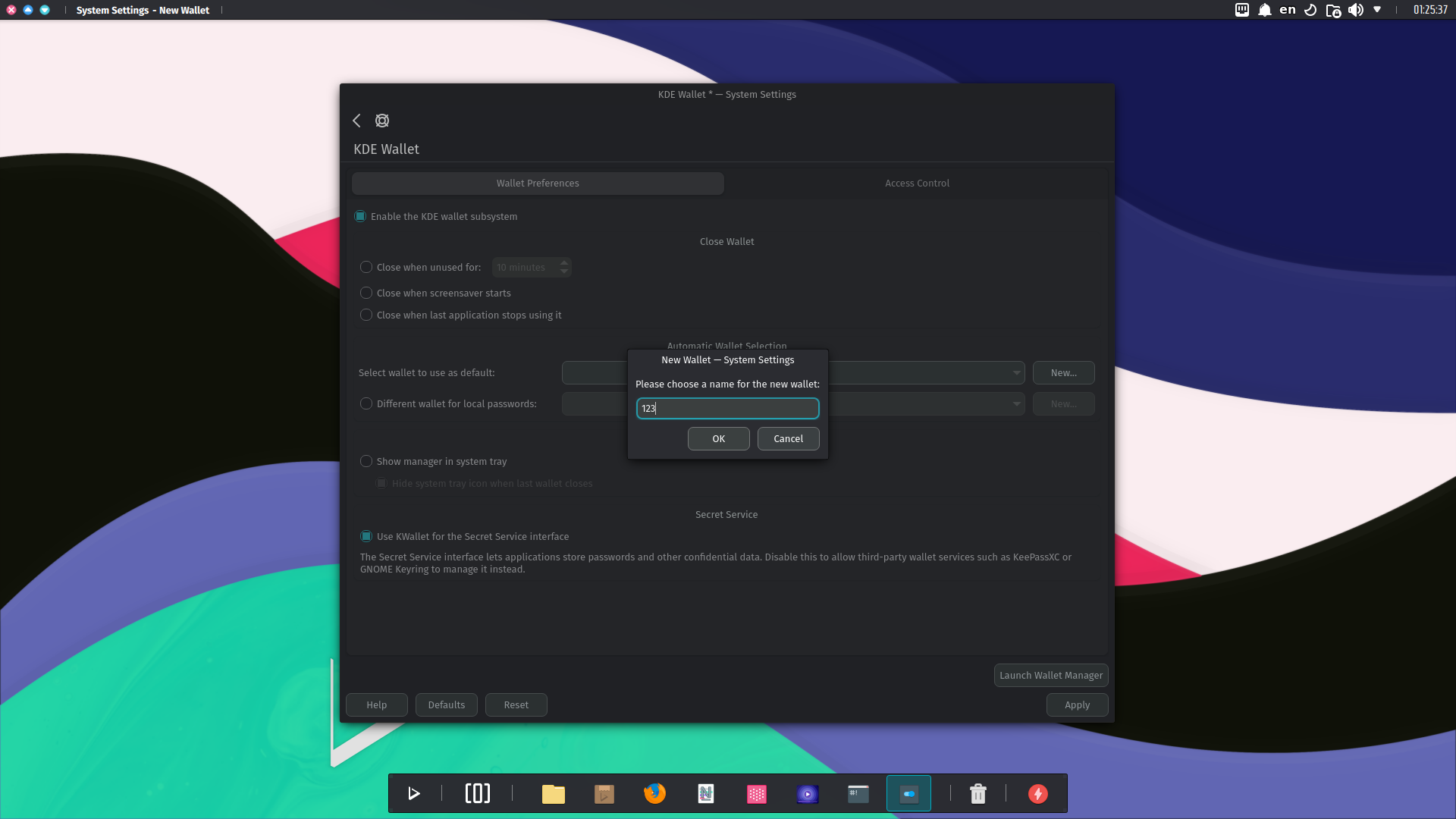
Next, use the New button in the KDE Wallet module in System Settings, and enter a name for the wallet.
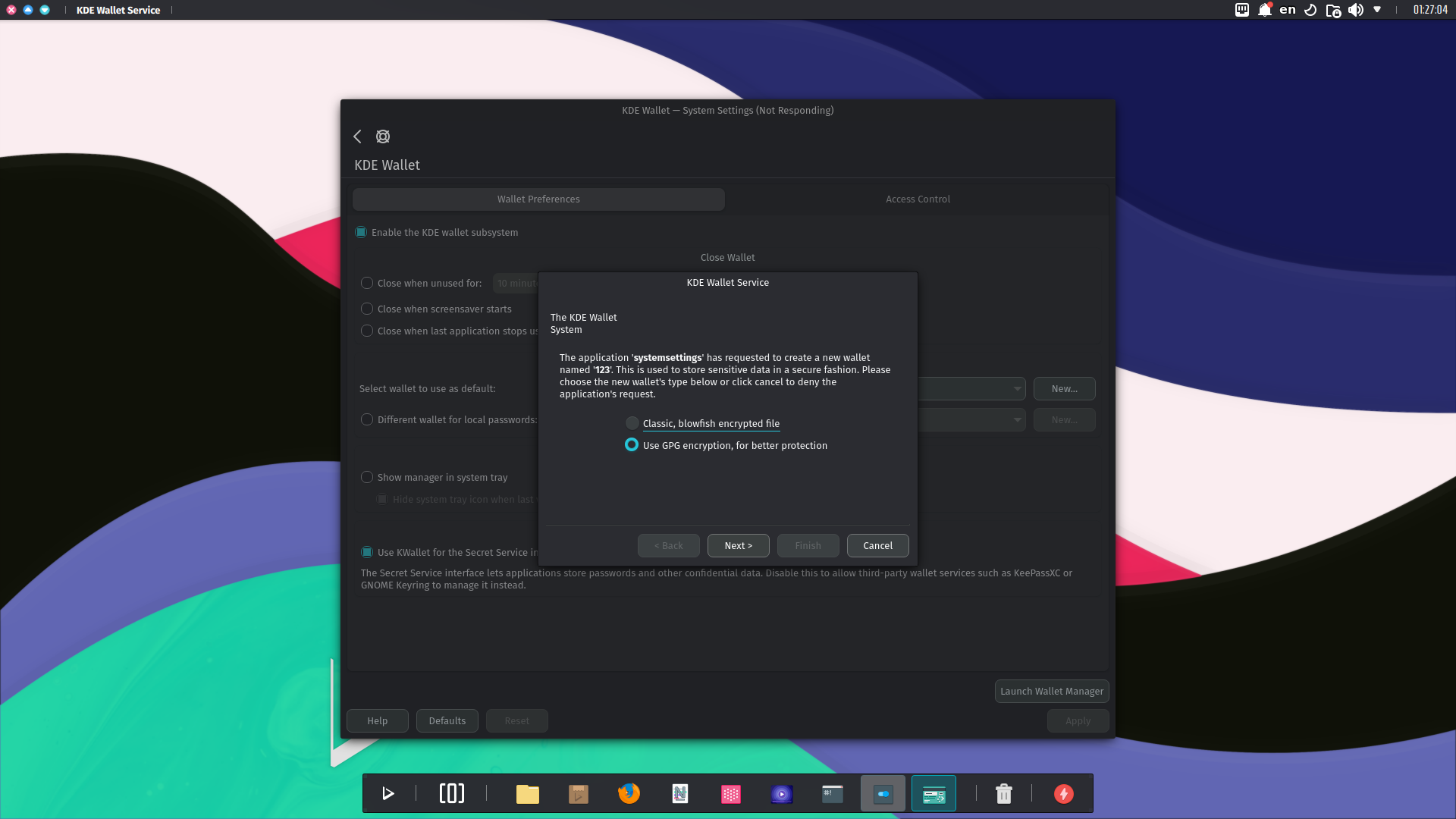
Then select the encryption method to secure the wallet.
- Blowfish. KWallet saves this sensitive data in a strongly encrypted file, accessible by all applications and protected with a master password we define.
- The Blowfish symmetric block cipher encrypts the data; the SHA-1 hash of the password to derive the key, which has a critical length of 156 bits (20 bytes). The data in the wallet file is also hashed with SHA-1 and checked before it is decrypted and made accessible to applications.
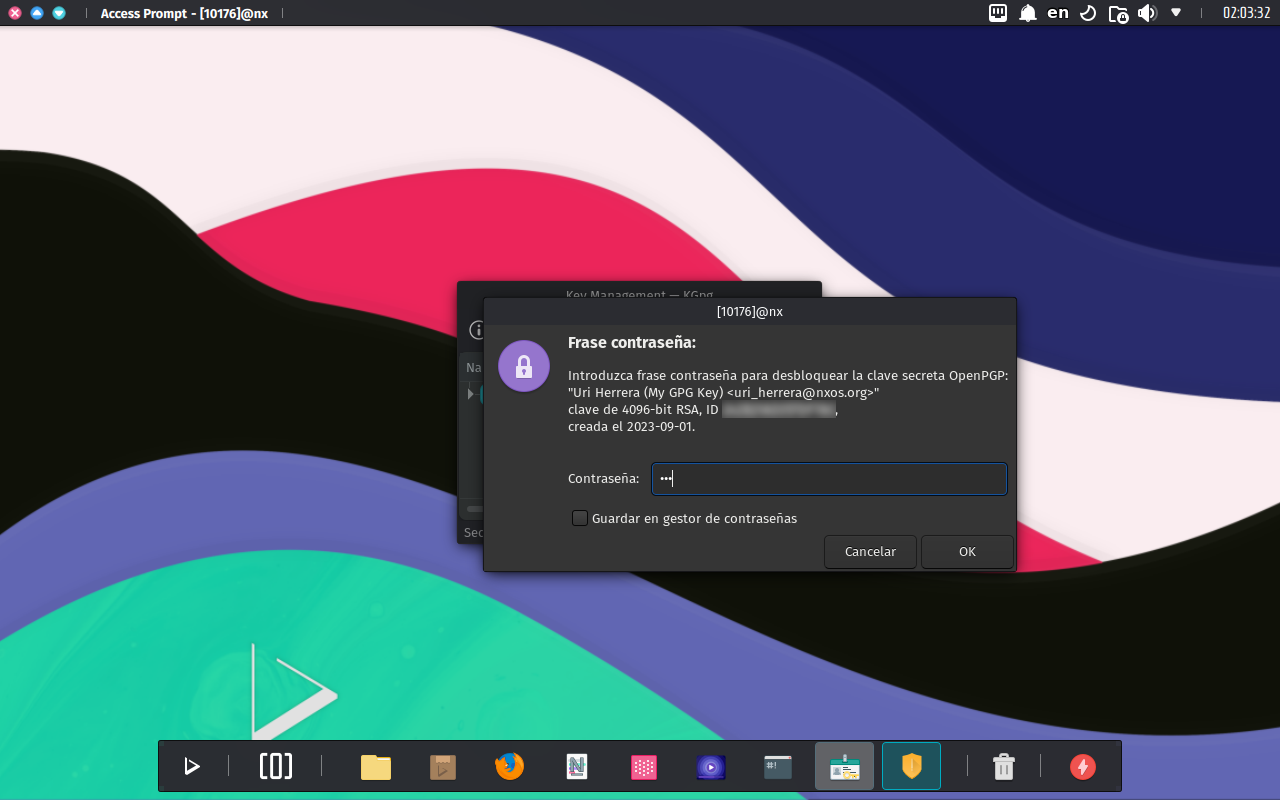
- GPG. GnuPG offers some powerful encryption algorithms and uses passphrase-protected long keys. If a GPG key is available, you will get the following dialog where you can select a key to use for your new wallet.
Since we created a GPG key, we’ll use it.
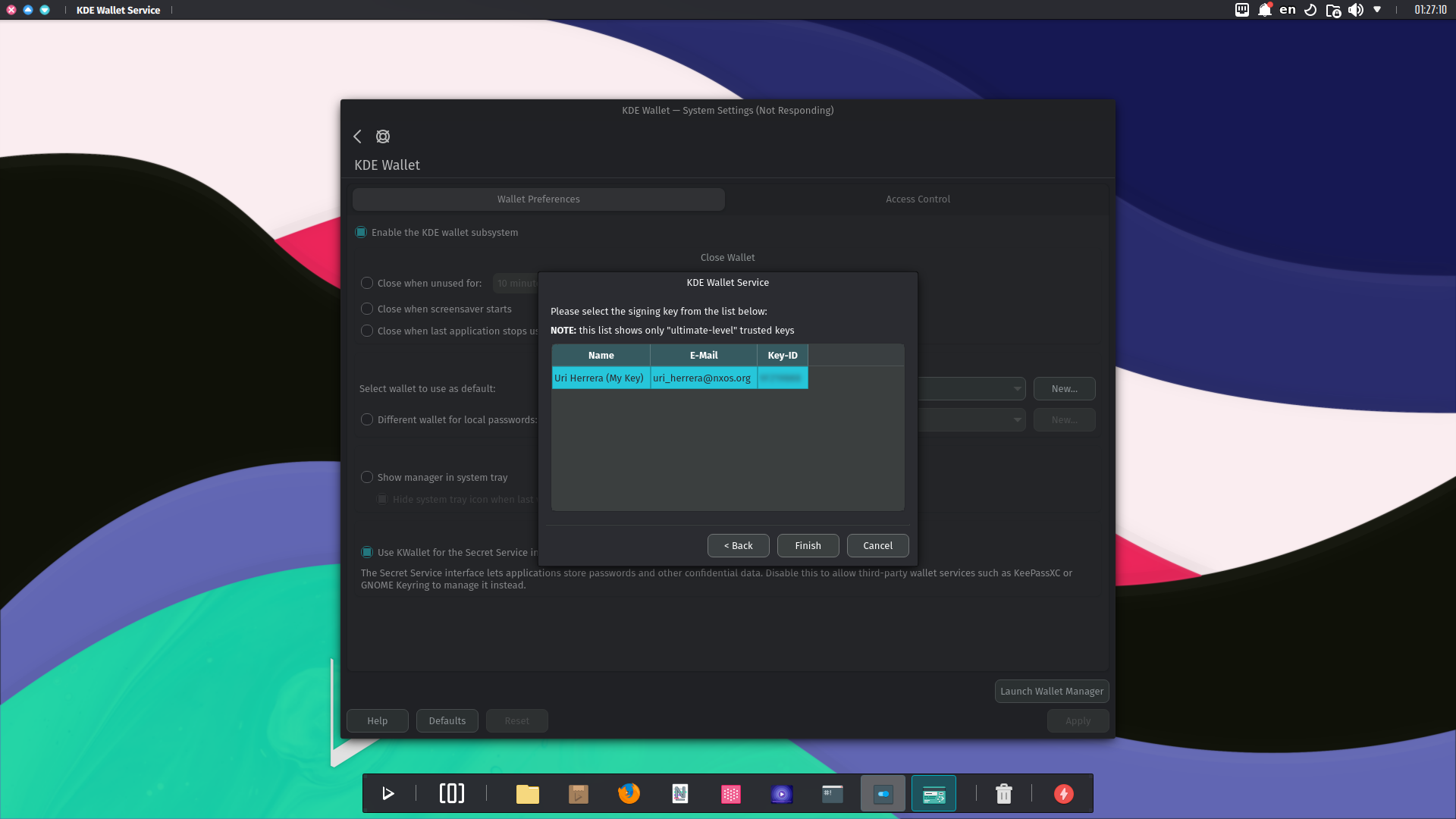
Finally, we click Finish. Now, KWallet will use GPG for wallet storage and opening. The passphrase dialog only shows once. Even if the wallet is closed after the initial opening, subsequent opening will occur silently during the same session.
Disclaimer: We do not develop KWalletManager, the KDE Wallet KCM, the KWallet subsystem, or KGpg. To request features or report problems, please create issues in the KDE bug tracker.
For more information about KWallet, check the KWallet Handbook.
That’s it; this concludes today’s tutorial.
