Today is the day! — Nitrux 2.8.1 “sc” is available to download
We are pleased to announce the launch of Nitrux 2.8.1. This new version combines the latest software updates, bug fixes, performance improvements, and ready-to-use hardware support.
Nitrux 2.8.1 is available immediately.
🔰 Information: The codename for this release is “sc,” which stands for “safer computing,” as it includes various changes focused on protecting distribution users and tools to protect their privacy and anonymization online in addition to the already existing encryption features from previous releases.
⚠️ Important: Despite the efforts and improvements in this release, we’re not claiming to be security or forensic experts or that the distribution is “impenetrable” or “unhackable,” so there isn’t any misunderstanding. Suggestions to continue improving on this area are welcome at our bug tracker (open a new discussion).
This release is brought to you by our friends at packagecloud. packagecloud provides Nitrux Latinoamericana with the vital infrastructure that allows us to build our distribution.
Lightning-fast, secure, automated package management.
📜 Table of Contents
✨ What’s new
We recommend new users do a fresh installation using the latest media. For users of the previous version (2.8.0), please check the Notes.
- To know where to check for a more detailed list of updated packages, please check the Notes.
Nitrux 2.8.1 build.310523.sc uses Linux 6.3.4-1 (Liquorix)
We’ve updated the following components of the distribution. For other information, see Notes.
- KDE Plasma to version 5.27.5, KDE Frameworks to version 5.106.0, and KDE Gear to version 23.04.1.
- Firefox to version 113.0.2.
- We’ve updated MESA to version 23.2~git2305280600.92a7cb~oibaf~j; see MESA Information.
- We’ve switched to Plasma Wayland, now the default graphical session.
- We decided to switch to the Wayland session since KDE now focuses on improving support for Wayland in various areas for the next release of Plasma. Additionally, Maui Shell is being developed primarily for Wayland with future support for XWayland.
- 🔰 Information: The Plasma X11 session is not listed in SDDM but can be restored; see Plasma X11 Session Information.
- 🔰 Information: Due to the differences in how application windows are managed in KWin Wayland to KWin X11, we’ve configured NX Desktop to detect which display server is used and load automatically specific settings for the window manager.
- For users with Nvidia GPUs, Latte Dock will not be utilized as the lack of maintenance of Latte Dock has caused an issue where the panels/dock are invisible when using the Plasma Wayland session and the Nvidia proprietary driver. A similar layout will be configured using Plasma panels; see the image below.
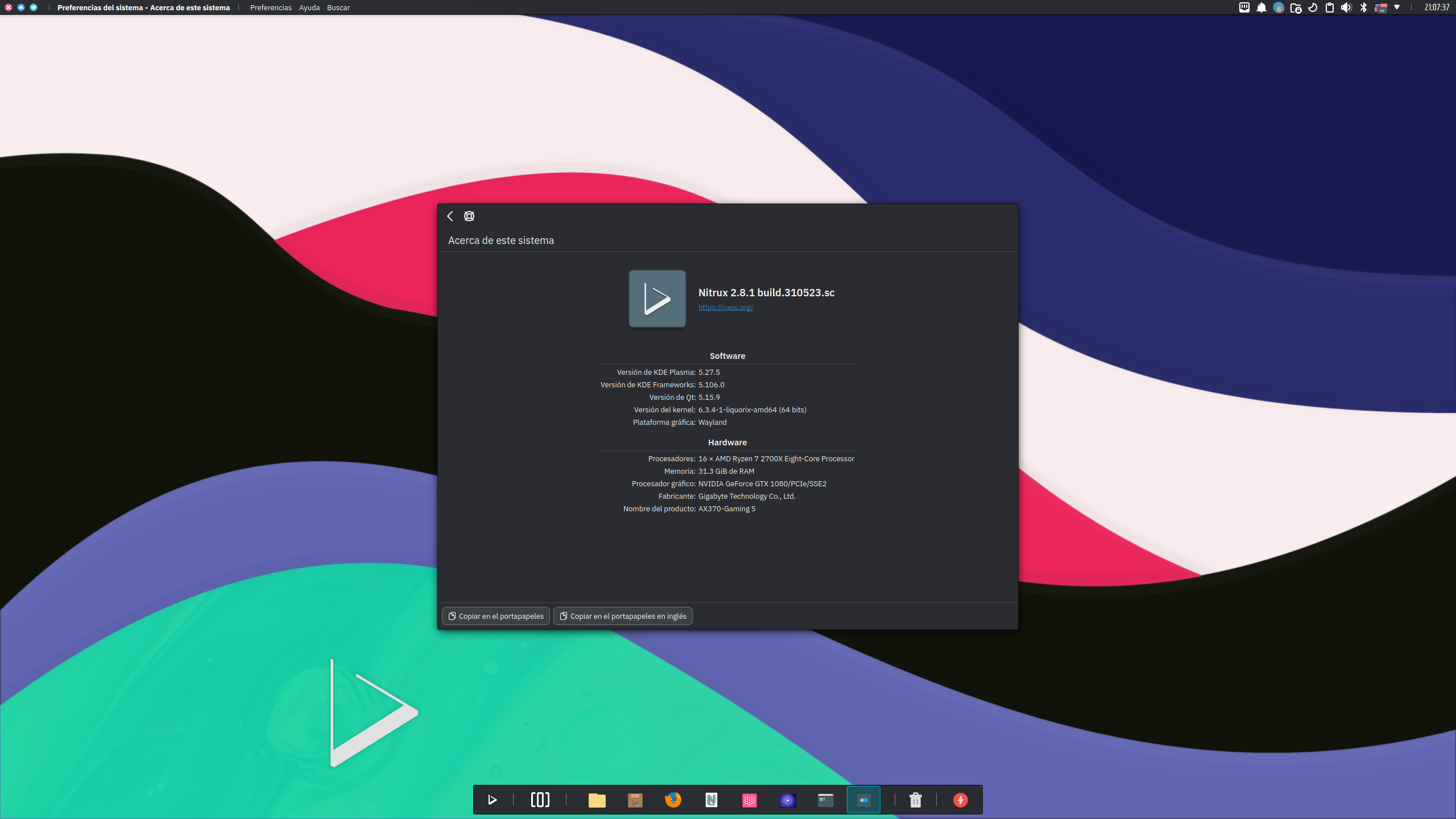
This layout is the default for users of Plasma Wayland and Nvidia graphic processors.
-
-
- For users of MESA drivers (AMD, Intel, etc.), Latte Dock will be utilized in the Plasma Wayland session but with the workaround noted in the Notes of the previous releases.
- For users who choose to use X11, no changes were made.
- ⚠️ Important: There are many bugs still in Plasma Wayland, especially if using an Nvidia GPU, including but not limited to applications that don’t work and missing features; we’ve listed some of the bugs we’ve found on the bug tracker; see Known Issues.
- We strongly recommend that users with Nvidia GPUs switch to the Plasma X11 session if these bugs are showstoppers for them.
- We also recommend reporting issues to both KDE and Nvidia regarding Wayland.
- ⚠️ Important: If selected during the installation, Calamares cannot enable the autologin feature due to using the Plasma Wayland session as default; see Known Issues.
-
Disclaimer: We do not develop KWin, Plasma, Calamares, the Nvidia proprietary driver, or the Wayland protocol. Please report bugs at their respective bug trackers.
- We’ve added the Industrial I/O subsystem proxy to D-Bus, which provides support for devices that, in some sense, are analog to digital or digital to analog converters. The Industrial I/O subsystem is intended to serve as a proxy, providing access to these devices through a D-Bus interface.
- 🔰 Information: Many ultrabooks ship with some of the devices listed below. Adding this subsystem will allow KWin Wayland to rotate the device screen automatically where supported.
- Devices that fall into this category are:
- ADCs.
- Accelerometers.
- Gyros.
- IMUs.
- Capacitance to Digital Converters (CDCs).
- Pressure Sensors.
- Color, Light, and Proximity Sensors.
- Temperature Sensors.
- Magnetometers.
- DACs.
- DDS (Direct Digital Synthesis).
- PLLs (Phase Locked Loops).
- Variable/Programmable Gain Amplifiers (VGA, PGA).
- Devices that fall into this category are:
- 🔰 Information: Many ultrabooks ship with some of the devices listed below. Adding this subsystem will allow KWin Wayland to rotate the device screen automatically where supported.
- We’ve added a parameter to make AppArmor always load by default and enabled the service for OpenRC.
- 🔰 Information: We already included AppArmor, but it was not enabled by default.
- 🔰 Information: Firejail (the sandbox program used for AppImages) supports AppArmor.
- We’ve added DNSCrypt-Proxy 2, including a service file for OpenRC. DNSCrypt-Proxy 2 is “A flexible DNS proxy, with support for modern encrypted DNS protocols such as DNSCrypt v2, DNS-over-HTTPS, Anonymized DNSCrypt and ODoH (Oblivious DoH).”
- The following is a list of features of DNSCrypt-Proxy.
- DNS traffic encryption and authentication.
- Supports DNSCrypt, DNS-over-HTTPS (DoH) using TLS 1.3, Anonymized DNS, and Oblivious DoH (ODoH).
- Local DOH Server.
- DNS query monitoring, with separate log files for regular and suspicious queries.
- Filtering: block ads, malware, and other unwanted content. Compatible with all DNS services.
- Time-based filtering with a flexible weekly schedule.
- Transparent redirection of specific domains to specific resolvers.
- DNS caching to reduce latency and improve privacy.
- 🔰 Information: DNSCrypt-Proxy is not enabled by default. To configure DNSCrypt-Proxy, see Security, Privacy, and Anonymization Features Information.
- The following is a list of features of DNSCrypt-Proxy.
- We’ve added Tor (not to be confused with Tor Browser) and Torsocks. “Tor is a connection-based low-latency anonymous communication system.” Meanwhile, “Torsocks allows you to redirect network traffic of individual SOCKS-friendly applications through the Tor network.”
- 🔰 Information: To route connections to the Tor network using Torsocks, see Security, Privacy, and Anonymization Features Information.
- We’ve adjusted Sysctl settings for better security by doing the following changes.
- Disable core dumps. Core dumps are created for diagnosing and debugging errors in Linux applications. However, core dumps may contain sensitive info, such as passwords and user data, including PAN, SSN, or encryption keys. Also, they take up a large amount of disk space too.
- Disable core dumps. Core dumps are created for diagnosing and debugging errors in Linux applications. However, core dumps may contain sensitive info, such as passwords and user data, including PAN, SSN, or encryption keys. Also, they take up a large amount of disk space too.
- To improve the security of user accounts, we’ve implemented the following login.defs and PAM parameters and policies comparatively to Debian.
- We’ve changed the expiration date of passwords. Passwords are the primary key to accessing an account, related services, and information, and therefore they need to be protected via a strong password and password expiry policy. The default expiration date of passwords in Debian is 99999 days; ours is 1111.1x shorter.
- We’ve increased the hashing rounds for passwords in login.defs and PAM. With over 60k rounds, it is more difficult to brute force the password; by default, Debian uses 5000 rounds which is too low for modern hardware.
- We’ve set the password hashing algorithm to SHA-2 512. Contrary to Debian, which uses yescrypt by default.
- We’ve increased the complexity of new passwords using PAM. This rule is not enforced in Debian, but it is enforced in Nitrux starting with this release.
- We’ve disabled unused network protocols, such as dccp, rds, sctp, and tipc, via the modprobe configuration to ensure they aren’t misused.
- We’ve added the Advanced Intrusion Detection Environment or AIDE. “AIDE is an intrusion detection system that detects changes to files on the local system. It creates a database from the regular expression rules that it finds from the config file.”
- The following is a list of features of AIDE.
- Supported message digest algorithms: md5, sha1, rmd160, tiger, crc32, sha256, sha512, whirlpool (additionally with libmhash: gost, haval, crc32b).
- Supported file attributes: File type, Permissions, Inode, Uid, Gid, Link name, Size, Block count, Number of links, Mtime, Ctime, and Atime.
- If support is compiled, support for POSIX ACL, SELinux, XAttrs, and Extended file system attributes.
- Plain text configuration files and database for simplicity.
- Powerful regular expression support to selectively include or exclude files and directories to be monitored.
- Gzip database compression if zlib support is compiled in.
- Stand-alone static binary for easy client/server monitoring configurations.
- 🔰 Information: To initialize AIDE, see Security, Privacy, and Anonymization Features Information.
- The following is a list of features of AIDE.
- We’ve added support for managing Btrfs partitions.
- ⚠️ Important: While this change allows Btrfs to be used in Calamares, please be aware that selecting Btrfs as the filesystem in Calamares for any partitions other than the ESP and the Swap after selecting the Manual partitioning mode will result in any of the filesystem features, including performance enhancements and encryption capabilities that we’ve enabled, not being utilized.
- We’ve added the GNU C Compiler version 11 (11.3.0) for software that requires it, like VMWare Workstation and VMWare Player, which do not support the GNU C Compiler version 12 included by default.
- We’ve added support for running the distribution using Hyper-V.
- This support also includes hyperv-daemons, a suite for Linux guests running on Hyper-V, consisting of hv_fcopy_daemon, hv_kvp_daemon, and hv_vss_daemon. And it also includes kernel modules (hv_vmbus, hv_storvsc, hv_blkvsc, hv_netvsc) in the initram to use with Hyper-V Linux Integration Services.
- We’ve added Rsyslog, a multi-threaded implementation of syslogd (a system utility providing support for message logging).
- We’ve updated the AMD Open Source Driver for Vulkan to version v-2023.Q2.2.
- We’ve added the LFS extension for Git.
- We’ve added xdg-desktop-portal-gnome, which is “A backend implementation for xdg-desktop-portal for the GNOME desktop environment” to avoid an issue with font rendering in Plasma Wayland and Flatpak applications.
We’ve fixed or closed the following issues in the distribution; see Report bugs.
- [Closed] Nvidia GPUs appear as llvmpipe when using the Plasma Wayland session #106.
- [Closed] The KDE PolicyKit authentication agent does not work on the Plasma Wayland when using the Nvidia proprietary driver #109.
We’ve removed the following components from the distribution.
- –
📥 Download
Here are various ways to download our ISOs and virtual appliances.
- ISO — Direct HTTP Download from our server.
- FOSS Torrents (Torrent).
- Sourceforge (mirror).
- OSDN (mirror).
Checksums (MD5).
7cc7bc718c8119d28df90540d46beb42 nitrux-nx-desktop-plasma-fb646131-amd64.iso 0x0fffffffnotreleasedyet12345789 nitrux-maui-shell-0x0fffff-amd64.iso
⛔ Known issues
To see a list of known issues, click here.
🗒 Notes
To see a list of release notes, click here.
🐞 Report bugs
To report bugs, please use our bug tracker on GitHub.
📝 Changelog history
To see a list of previous changelogs, click here for the changes archived at our site or for the changes archived at Sourceforge.
📰 Resources
Here are various articles, tutorials, and other information on our blog.
📌 Post-release announcements
Here’s a list of post-release service announcements for this version of Nitrux.