In today’s tutorial, we’ll check all the filesystem, security, privacy, and anonymization features in Nitrux.
Difficulty: ★☆☆☆☆
📜 Table of Contents
-
- Default Security Policies in Nitrux
- XFS Features and Root Immutability in Nitrux
- Using and Configuring AIDE
- Online Anonymization using Tor and DNSCrypt-Proxy 2
- Importing an OpenVPN connection in NetworkManager
- Ad-blocking in Nitrux using dbab
- File Encryption in Nitrux
- Using F2FS Features in Nirux
- Using Fingerprint Authentication in Nitrux
Default Security Policies in Nitrux
Nitrux enables the following security features and policies by default and any encryption capabilities (enabled by Nitrux™).
- Features:
- Application sandboxing.
- AppImages and other executables.
- Flatpaks.
- Network security.
- Firewall (UFW), using Plasma Firewall.
- OpenVPN, OpenConnect, and Fortinet SSLVPN/OpenFortiVPN support in NetworkManager.
- Wireguard support.
- DNS leak prevention, using DNSCrypt-Proxy 2.
- DNS-based Ad blocking, using dbab.
- Filesystem immutability and root directory intrusion detection.
- Password management.
- KWalletManager. KWalletManager is a tool to manage the passwords on your system.
- 🔰 Information: To use KWalletManager with GPG keys, we recommend creating a key using KGpg. To do this, see our tutorial on How to use KWalletManager in Nitrux.
- Fingerprint support in SDDM via fprint.
- 🔰 Information: You can check if your device is supported by checking the list of supported or unsupported devices. The list of supported devices is not updated regularly and is not complete.
- KWalletManager. KWalletManager is a tool to manage the passwords on your system.
- Application sandboxing.
- Policies:
- Disable core dumps. Core dumps are created to diagnose and debug errors in Linux applications. However, they may contain sensitive Information, such as passwords and user data, including PAN, SSN, or encryption keys. They also take up a large amount of disk space.
- Stricter password expiration date. Passwords are the primary key to accessing an account, related services, and data, and therefore, they need to be protected via a strong password and password expiry policy. The default expiration date of passwords in Debian is 99999 days; ours is 1111.1 times shorter.
- Increase the number of hashing rounds for passwords. With over 60k rounds, it is more difficult to brute-force the password; by default, Debian uses 5000 rounds, which is too low for modern hardware.
- Passwords use SHA-2 512 encryption. Contrary to Debian, which uses yescrypt by default.
- New passwords must be made more complex. This rule is not enforced in Debian. However, it is in Nitrux, starting with version 2.8.1.
- Deactivate the root account in the Live session and on the installed system. By default, Nitrux does not add or enable a password for the root account. Any administrative tasks performed by the user must be done using sudo.
- Enforce a stricter password quality policy. By default, we use libpwquality to increase user account security during installation and for user accounts created post-installation. With sufficient randomness, these passwords must be over eight characters long, including uppercase and lowercase letters, numbers, and symbols.
- Enable BPF JIT hardening if the JIT is enabled: Enabling hardening for the Berkeley Packet Filter (BPF) Just-in-time (JIT) compiler aids in mitigating JIT spraying attacks.
- Fill freed pages and heap objects with zeroes: Ensure that when freed, they are filled with zeroes, enhancing security by preventing data leaks through uninitialized memory.
- Disable merging of slabs of similar sizes: Preventing the kernel from merging memory slabs of similar sizes can improve security by making it harder for attackers to exploit specific memory corruption vulnerabilities.
- Disable Virtual Syscalls: This option disables virtual Syscalls and system calls implemented in user space for performance reasons, potentially reducing the attack surface for specific exploits.
- Randomize kernel stack offset on syscall entry: Introduce randomness to the kernel stack offset whenever a system call is made, adding another layer of security by making it harder for attackers to predict memory addresses.
- Enable MAC addresses randomization mode. MAC randomization can be used for increased privacy by not disclosing the actual MAC address to the network.
- Enable IPv6 Privacy Extensions standard. With privacy extensions, the kernel generates a temporary address mangled from the original autoconfigured address. Private addresses are preferred when connecting to a remote server to hide the original address.
- Enable Reverse Path Filtering. It prevents IP spoofing attacks, enhances security, and reduces vulnerability to DDoS attacks.
- Disable Source Routing. Prevents IP spoofing and strengthens security by turning off source routing, blocking potential bypassing of security controls.
- Restricts access to kernel pointer addresses. Improves security by restricting access to kernel pointer addresses to privileged processes, preventing information leaks.
- Turn off the SysRq key. This enhances security by preventing unauthorized system commands.
- Enable Page Table Isolation. Mitigates speculative execution attacks like Meltdown.
XFS Features and Root Immutability in Nitrux
The root partition will use the XFS filesystem. This XFS-formatted partition will also use the following additional filesystem features (enabled by Nitrux™).
- Allow inodes to be placed at any location on the filesystem. Storing a file’s inode in the exact location as the file’s data improves performance.
Additionally, by default, Nitrux performs filesystem checks and repairs (if needed) during boot time.
Since Nitrux 2.6.0, the root directory is set to be immutable by default, meaning no changes occur to its contents. This change allows us to provide new versions of the distribution with a higher degree of certainty that no changes have happened to the root that might cause a conflict. We also want to avoid sudden issues from upgraded packages coming from a different origin than our repository, which we have a minimal way of controlling. However, we understand that there may be cases where users need to change something in the root directory.
- ⚠️ Important: Avoid writing data to the root as a user while using the command below, as this will cause an error when exiting the shell session that overlayroot-chroot will create. Any changes to the root directory should be explicitly done only through the shell session after running overlayroot-chroot.
- ⚠️ Important: Mounting /dev is essential; otherwise, stuff like the CLI text editor we include in Nitrux (micro) will not work. Depending on the task to be completed, other filesystems must be mounted, e.g., /var/lib, /home, /tmpfs, etcetera. Only /proc, /run, and /sys are mounted by default.
- 🔰 Information: After making the desired modifications, unmount the filesystems and exit.
sudo overlayroot-chroot # Filesystems to mount; /dev is strictly necessary. mount -t devtmpfs dev /dev # To mount the partitions created by our Calamares configuration use findfs and the partition label. mount -t auto $(findfs LABEL=NX_VARLIB) /var/lib # (... do stuff...) sync # Unmount the partitions. umount /dev /var/lib exit
Changes are immediately applied to the root, i.e., the lower directory. However, for the changes to be applied to the overlay, i.e., the upper directory, the computer must be rebooted, or the kernel must be loaded again using Kernel Boot (where supported); otherwise, any modifications won’t be visible.
Alternatively, users can temporarily boot with the immutability disabled. To do that, do the following steps.
- ⚠️ Important: We must stress that the preferred method to modify the root is the above. If you know what you’re doing, use the technique below at your own risk.
- Press E in the GRUB boot menu.
- Using the arrow keys, navigate the text and find the kernel parameter
overlayroot=tmpfs:swap=1,recurse=0, and change the parameter tooverlayroot=disabled. - To continue the boot process, press F10.
- After making the desired modifications, reboot.
Disclaimer: The user is responsible for any manual and permanent changes to the root using either of the methods mentioned in this section. If these changes create conflicts when upgrading using the Nitrux Update Tool System, users are expected to resolve these conflicts independently. Please do not open issues regarding this use case in the bug tracker; they will be closed.
Using and Configuring AIDE
Since Nitrux 2.6.0, the distribution’s root directory has been immutable by default; however, in Nitrux 2.8.1, the distribution includes the Advanced Intrusion Detection Environment (AIDE) as an additional security feature. “AIDE is an intrusion detection system that detects changes to files on the local system. It creates a database from the regular expression rules that it finds from the config file.” AIDE can also be configured to monitor other directories; please check the AIDE manual.
- ⚠️ Important: The commands below create, copy, edit, or move files in the root directory; see XFS Features and Root Immutability in Nitrux.
To start using AIDE, run the following command. The command below will create the database AIDE uses to compare file changes.
- ⚠️ Important: Creating the AIDE database will take several minutes. Do not stop the process, i.e., do not close the terminal window, log out, shut down, or reboot the computer, or the process will have to be restarted.
aide -i -c /etc/aide/aide.conf
- Next, install the newly generated database with the following command.
cp /var/lib/aide/aide.db.new /var/lib/aide/aide.db
- After creating the database, users can run the commands below to look for changes in the root directory.
- Run the following command to check the database after adding or editing a file to the root.
aide -C -c /etc/aide/aide.conf
- Run the following command to check and update the database after adding or editing files in the root.
aide -u -c /etc/aide/aide.conf
Online Anonymization using Tor and DNSCrypt-Proxy 2
Since Nitrux 2.8.1, the distribution includes Tor, Torsocks, and DNSCrypt-Proxy 2 to help users protect their online presence.
- ⚠️ Important: To use Tor, start the service in OpenRC; see our tutorial, How to create service files in Nitrux pt. 1: OpenRC.
- 🔰 Information: When using Tor and Torsocks, the Internet speed of the connection will be slower; this is not a bug in Nitrux. The slower speed is an expected side-effect of using a proxy.
Configure Torsocks in Plasma
To use Tor (via Torsocks) in Plasma, do the following.
- Go to System Settings→Settings→Proxy and select “Use manually specified proxy configuration.”
- Go to SOCKS Proxy, type localhost, select port 9050, and click the Apply button.
- ⚠️ Important: Not all applications will use this proxy setting, notably Firefox, Chromium, or anything derived from them. Some applications may allow the proxy to be configured in their settings.
Configure Torsocks in Firefox
To use Tor with Firefox, check “Connection settings in Firefox” on the Firefox Support website.
- Select Manual configuration, then in SOCKS Proxy, type localhost, select port 9050, and check SOCKS v5.
Configure DNSCrypt-Proxy 2 system-wide
To use DNSCrypt-Proxy 2 system-wide, do the following.
- First, replace the listen address that DNSCrypt-Proxy 2 uses by default.
- ⚠️ Important: The commands below create, copy, edit, or move files in the root directory; see XFS Features and Root Immutability in Nitrux.
sed -i 's+:5300+127.0.0.1:53+g' /etc/dnscrypt-proxy/dnscrypt-proxy.toml
- Since Nitrux 3.5.0, Dnsmasq has been running as a plugin for NetworkManager. To stop using it and thus free the port necessary for DNSCrypt-Proxy, make the following change to the NetworkManager configuration.
sed -i 's+dns=dnsmasq+dns=none+g' /etc/NetworkManager/conf.d/00-dns.conf
- Then, kill Dnsmasq. It will conflict with DNSCrypt-Proxy 2 because it will not allow it to use port 53.
sudo killall dnsmasq
Run the DNSCrypt-Proxy 2 command in the background.
sudo dnscrypt-proxy -config /etc/dnscrypt-proxy/dnscrypt-proxy.toml &
- Next, go to System Settings→Connections→Your Connection→IPv4 and select “Automatic (only addresses)“ as the method.
- Then, enter the localhost address, 127.0.0.1, in the DNS Servers field. Repeat for IPv6 and click the “Apply” button.
- Restart the service for NetworkManager.
sudo rc-service network-manager restart
Next, edit the file /etc/resolv.conf with the following:
- ⚠️ Important: To prevent other software from overriding the file, make it immutable.
- ⚠️ Important: The command below creates, copies, edits, or moves files in the root directory; see XFS Features and Root Immutability in Nitrux.
bash -c 'cat > /etc/resolv.conf <<EOF nameserver ::1 nameserver 127.0.0.1 options edns0 single-request-reopen EOF' chattr +i /etc/resolv.conf
- Test that the DNS resolving is working. To test, run the following command.
- Verify that the resolver is not your ISP.
dnscrypt-proxy -config /etc/dnscrypt-proxy/dnscrypt-proxy.toml -resolve nxos.org
- Finally, to test using a web browser, by default Firefox, go to the following website, DNS leak test, and click “Extended test.” Like before, check that the resolvers are not your ISP.
- Optionally, create a service file that starts DNSCrypt-Proxy 2. To create services for OpenRC, see our tutorial, How to create service files in Nitrux pt. 1: OpenRC.
Please note the following when using DNSCrypt-Proxy 2.
- ⚠️ Important: DNSCrypt-Proxy 2 will help prevent DNS leaks. However, it does not hide the IP address; this is visible when visiting the site DNS leak test. To hide the IP address, use Tor or a VPN.
- 🔰 Information: When using DNSCrypt-Proxy 2, the Internet speed of the connection will be slower; this is not a bug in Nitrux. The slower speed is an expected side-effect of using a proxy.
Importing an OpenVPN connection in NetworkManager
Since Nitrux 2.7.0, the distribution includes the OpenVPN plugin for NetworkManager. To import an OpenVPN connection using a file, i.e., example-vpn.ovpn, do the following.
- Open System Settings→Connections.
- Click the add (+) button and scroll down until you find “Import VPN connection…”
- Click the button “Create” and select your .ovpn file.
- Select the new VPN connection and ensure that in connection type “Password with certificates (TLS)” is selected, then ensure that “Save password only for this user (cipher)” is selected for the secret key and VPN passwords.
- Activate the connection from the Connection settings (right-click → connect) or use the network icon in the system tray.
- ⚠️ Important: If you use some public VPNs to protect your privacy, you might get a public IP address or at least be exposed to external connections. Once a public VPN is enabled, you’re no longer protected by the firewalls in front of your computer. Nitrux already uses UFW and is enabled by default to ignore incoming connections to alleviate this issue.
- ⚠️ Important: Activating the connection immediately will cause a second dialog window to appear in the app, asking for the VPN password again after entering both passwords. To avoid this, log out and log in or reboot after adding the VPN connection.
- A dialog window will appear asking for two passwords; one is the VPN password, and the other is the secret key. Enter the password for the VPN and a password for the secret key.
- 🔰 Information: The password for the user account can be used as the password for the secret key.
- (Optional) Pair the VPN with a primary connection to connect to the VPN automatically. Go to System Settings→Connections→Your Connection→General configuration, check the box “Connect automatically to VPN,” select the VPN, and click “Apply.”
Please note the following when importing an OpenVPN connection.
- ⚠️ Important: IPv6 support depends on the VPN provider; this is not a bug in Nitrux. If the provider doesn’t support IPv6 tunneling, turn off IPv6 on the primary connection. Go to System Settings→Connections→Your Connection→IPv6, select “Ignored” as the method, and click “Apply.”
Ad-blocking in Nitrux using dbab
Since Nitrux 2.9.0, the distribution includes dbab, a Dnsmasq-based ad-blocking utility using Pixelserv. “dbab provides a solution for the SOHO service environment and smoothly integrates DHCP, DNS, local caching, and Ad blocking into harmony. Adblocking is done by DNSmasq + Pixelserv, i.e., done at the DNS level — all requests to ad sites are blocked right there at DNS.” Features include the following.
- Work at the DNS level. Leave the web pages intact without pattern matching, string substitution, or replacing HTML elements.
- Serve instantly. All ads will be replaced by a 1×1 pixel gif image served locally by the dbab-svr pixel server.
- Maintenance free. You don’t need to maintain the list of ad sites yourself. The block list can be downloaded from pgl.yoyo.org periodically. If you don’t like some of the entries, you can quickly add to or remove them from that list.
To download an updated block list, run the following command.
- ⚠️ Important: The command below creates, copies, edits, or moves files in the root directory; see XFS Features and Root Immutability in Nitrux.
dbab-get-list
To manually add or remove a domain from the block list, edit the following file.
- ⚠️ Important: The command below creates, copies, edits, or moves files in the root directory; see XFS Features and Root Immutability in Nitrux.
micro /etc/dnsmasq.d/dbab-map.adblock.conf
For Dnsmasq to use the lists created by dbab, these must be available in the correct directory; create a symlink to the directory /etc/NetworkManager/dnsmasq.d for each file if they don’t exist. Then, after any changes to the block list, restart Dnsmasq.
- 🔰 Information: Since Nitrux 3.5.0, Dnsmasq runs as a plugin of NetworkManager, so Dnsmasq will not load files from the directory /etc/dnsmasq.d but from /etc/NetworkManager/dnsmasq.d; create links to load the desired configuration files if they don’t exist.
- ⚠️ Important: The command below creates, copies, edits, or moves files in the root directory; see XFS Features and Root Immutability in Nitrux.
ln -sv /etc/dnsmasq.d/dbab-map.adblock.conf /etc/NetworkManager/dnsmasq.d/dbab-map.adblock.conf ln -sv /etc/dnsmasq.d/dbab-map.trashsites.conf /etc/NetworkManager/dnsmasq.d/dbab-map.trashsites.conf
- 🔰 Information: Since Nitrux 3.5.0, Dnsmasq runs as a plugin of NetworkManager. To reload the Dnsmasq configuration, disconnect from the network using the GUI, and restart the NetworkManager service. After restarting the service, close and reopen applications connected to the Internet, such as web browsers.
sudo rc-service network-manager restart
Finally, run dbab-svr to initialize the Pixelserv server.
sudo dbab-svr &
Optionally, enable the service file that starts dbab. To do this, run the following command.
- ⚠️ Important: The command below creates, copies, edits, or moves files in the root directory; see XFS Features and Root Immutability in Nitrux.
rc-update add dbab-openrc async rc-update -u
File Encryption in Nitrux
Nitrux provides multiple ways to encrypt data, including block-device using dm-crypt; see Installing Nitrux, filesystem-level using f2fscrypt and userland encryption tools like fscrypt and Plasma Vaults.
- As its name suggests, Plasma Vaults is tightly integrated with Plasma Desktop and can be accessed from the system tray.
- To create a new vault, click the system tray applet, then click ‘Create a new vault’ and follow the setup wizard.
- Plasma Vault supports the following encryption “engines:” CryFS (the default), EncFS (suitable for offline use), and gocryptfs (recommended).
- A non-GUI option is fscrypt. fscrypt (not to be confused with f2fscrypt) is a tool for managing the native file encryption support of the ext4, F2FS, and UBIFS file systems.
Using F2FS Features in Nitrux
Since Nitrux 2.8.0, the home and /var/lib partitions will use F2FS instead of XFS. These F2FS-formatted partitions will also use the following additional filesystem features (enabled by Nitrux™).
- Compression using zstd with compression at level 6. The primary goal is reducing writes to extend the flash lifetime and, potentially, a slight increase in performance.
- Verification of compressed blocks using a checksum to avoid corruption.
- Enable a better garbage collector and asynchronous garbage collection.
- Avoid synchronously updating access or modification times, which improves I/O performance and flash durability.
- Native F2FS file encryption. Encryption is applied at the directory level, and different directories can use different encryption keys. To use F2FS’s native encryption support.
Native File Compression in F2FS
F2FS allows the user to compress directories on-demand; to do this, run the following command.
chattr -R +c $DIRECTORY
Native File Encryption in F2FS
F2FS allows the user to use its native encryption capabilities through f2fscrypt and fscrypt.
- If using f2fscrypt, do the following.
- First, create the key in the keyring using a simple salt (or generate a random salt).
f2fscrypt add_key -S 0x1234 Enter passphrase (echo disabled): Added key with descriptor [28e21cc0c4393da1]
- Then, use it to set the policy for the directory to be encrypted.
f2fscrypt set_policy 28e21cc0c4393da1 /encrypted/dir Key with descriptor [28e21cc0c4393da1] applied to /encrypted/dir.
- After each reboot, the same command can be used to set the key for decrypting the directory and child directories.
f2fscrypt get_policy /encrypted/dir/ /encrypted/dir/: 28e21cc0c4393da1
- If using fscrypt, do the following.
-
- 🔰 Information: fscrypt is the preferred option over f2fscrypt; while both can manage F2FS native encryption features, f2fscrypt is deemed missing many essential features and is no longer actively developed.
- Run fscrypt so that it creates its configuration file and work directory.
-
sudo fscrypt setup
- Then, run the following command since the file system on which encryption is to be used is not the root file system.
- Where $MOUNTPOINT is where the file system is mounted, e.g.,/home.
sudo fscrypt setup $MOUNTPOINT
- This creates the $MOUNTPOINT/.fscrypt directory to store fscrypt policies and protectors.
- ⚠️ Important: Never delete the .fscrypt directory; otherwise, ALL access to encrypted files will be lost.
Using Fingerprint Authentication in Nitrux
Since version 3.4.1, Nitrux has included fprint, and since version 3.9.0, the necessary configurations for fingerprint authentication in SDDM and the Plasma lock screen, PolicyKit password dialogs, and sudo.
- ⚠️ Important: Note that fprint also has limitations regarding which fingerprint sensors will work with it; see the following link to verify that your sensor is supported by fprint. If the sensor is not supported, the button will not be available.
To enable this method of authentication, follow the following steps. Go to System Settings→Users and click Configure Fingerprint Authentication.
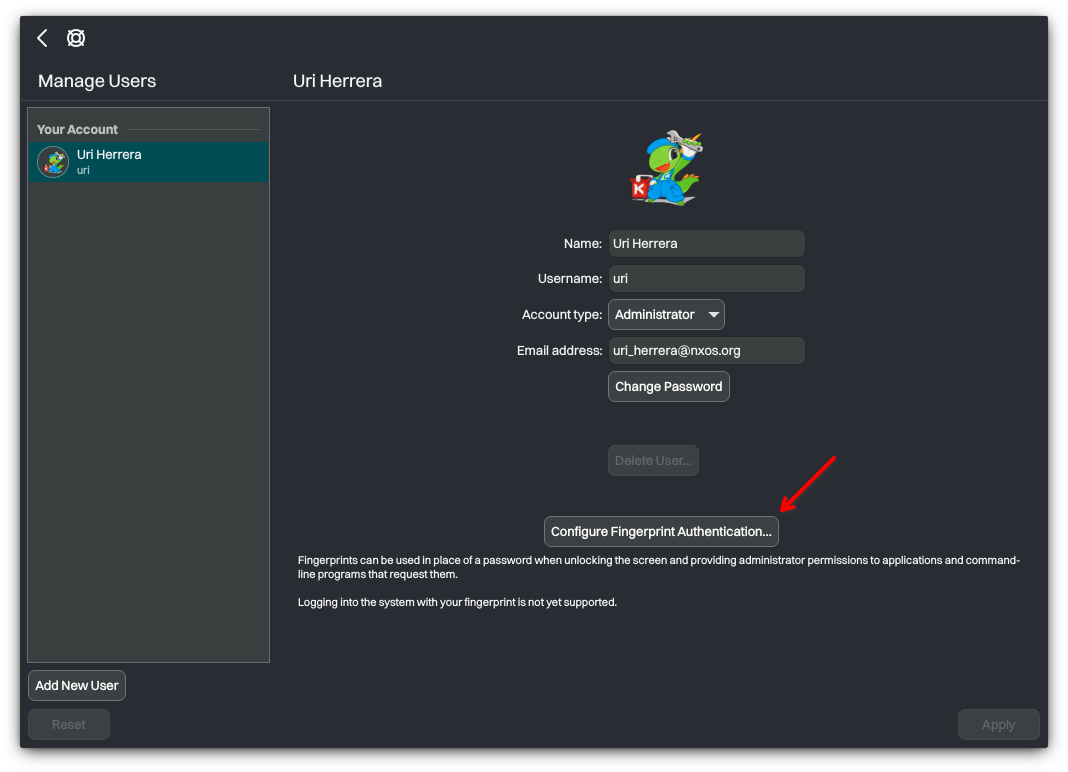
Then, click +Add to begin the process of enrolling a new fingerprint.
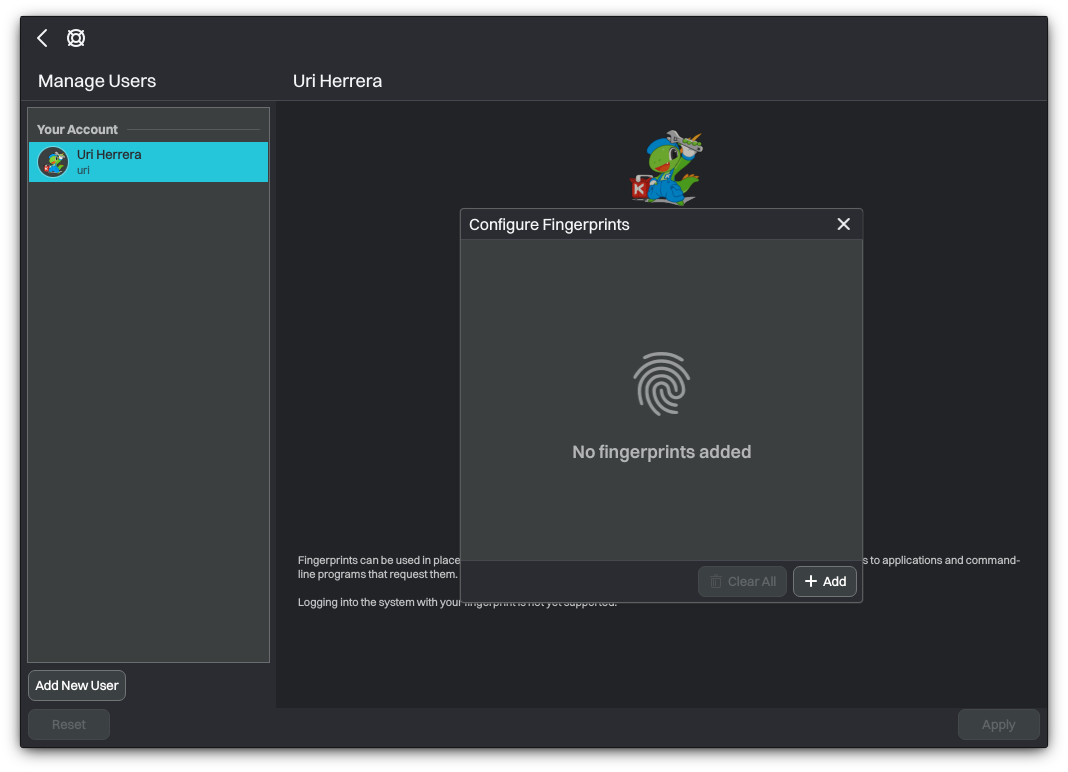
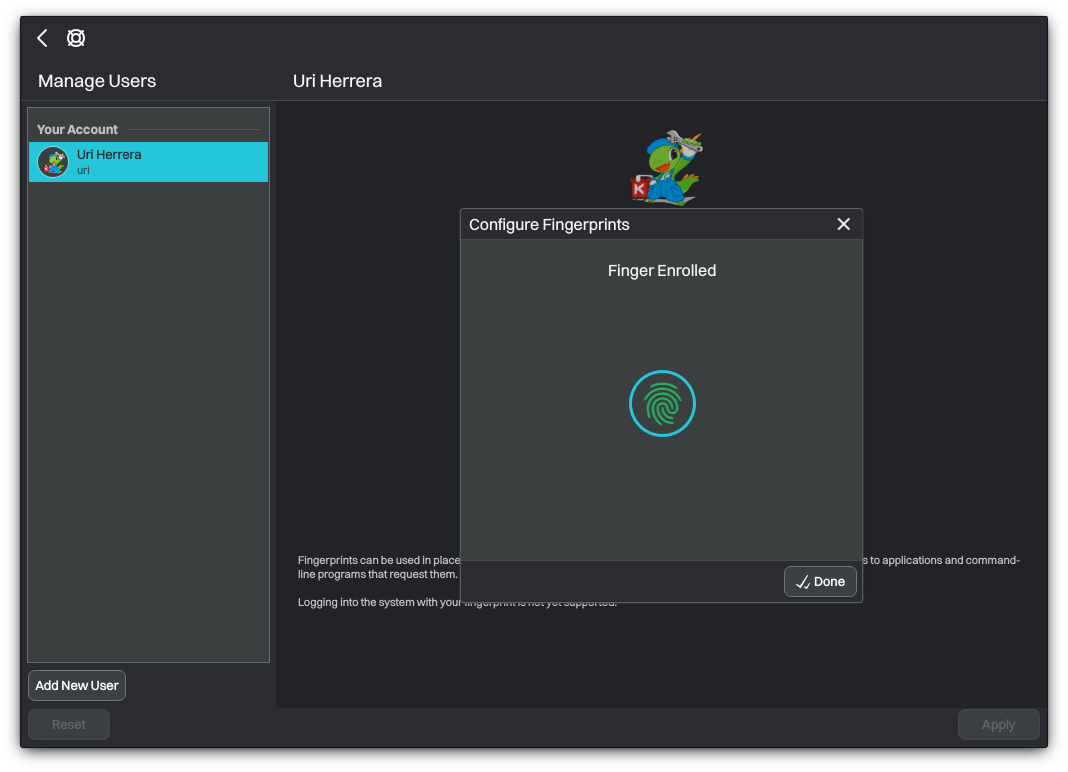
After successfully enrolling a new fingerprint, open the terminal and run the following command to update the necessary PAM configuration files.
- ⚠️ Important: The command below creates, copies, edits, or moves files in the root directory; see XFS Features and Root Immutability in Nitrux.
- ⚠️ Important: The command below requires the directory /var/lib to be mounted.
pam-auth-update
- 🔰 Information: Use the arrow keys to navigate and the spacebar to select an option. Finally, use Enter to select Yes on each screen.
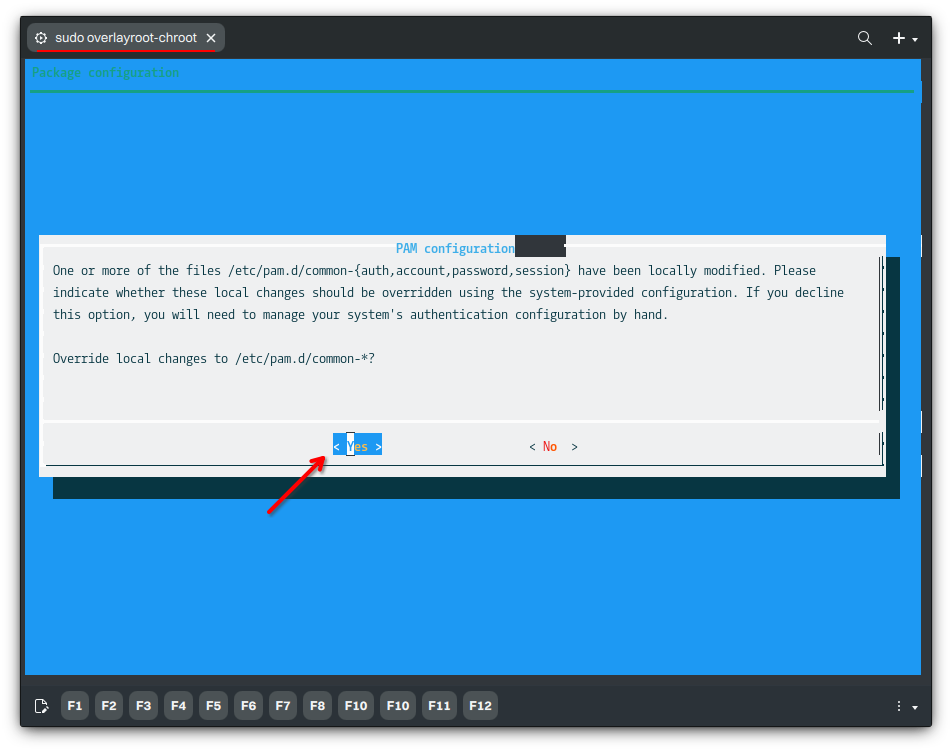
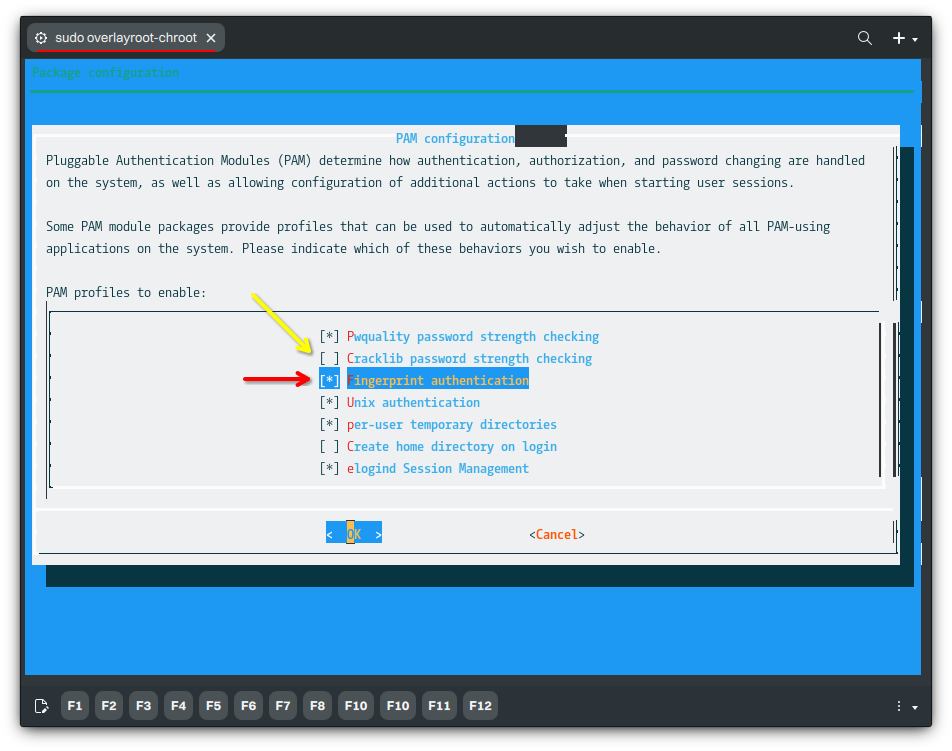
When selecting which PAM profile to enable, it’s essential to deselect Cracklib password strength checking and select Fingerprint authentication. Otherwise, fingerprint authentication can’t be used. After using Enter to select <OK>, proceed to reboot.
After rebooting, users can use fingerprint authentication to unlock the user session in SDDM (if autologin is disabled). However, SDDM does not indicate this is possible; this is not a bug in Nitrux.
- ⚠️ Important: SDDM works with a fingerprint reader when using fprint, and we have configured SDDM to use fingerprints or passwords to log in. However, be aware of the limitations of the current implementation of this functionality in SDDM; see this issue at the SDDM repository for more information.
To log in using the fingerprint, click the “Login” button and place your finger on the sensor; SDDM will automatically unlock the session.
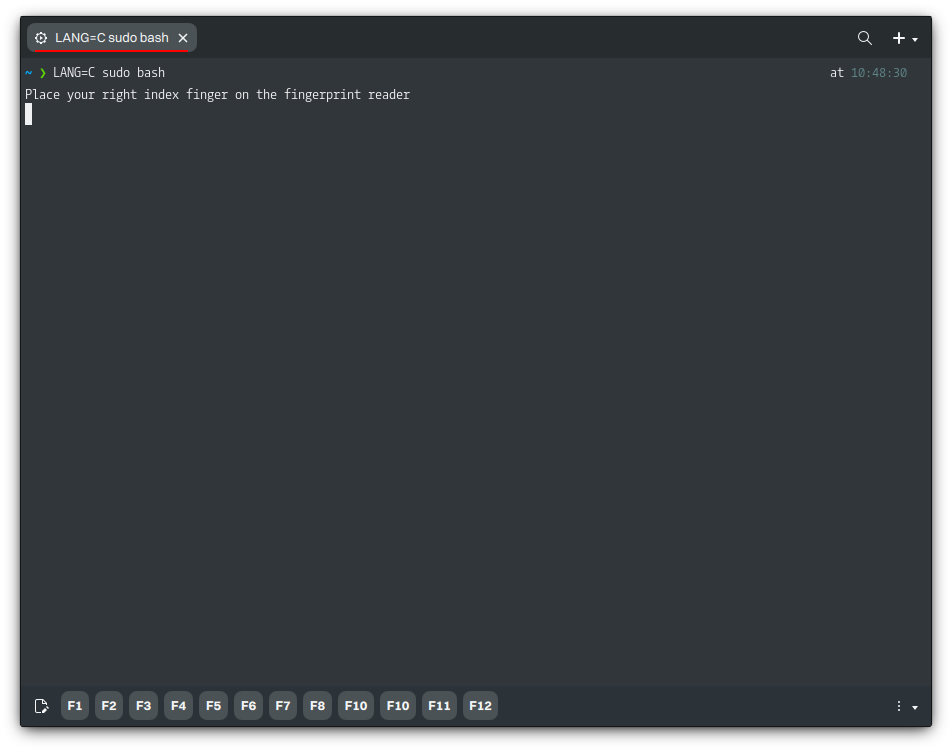
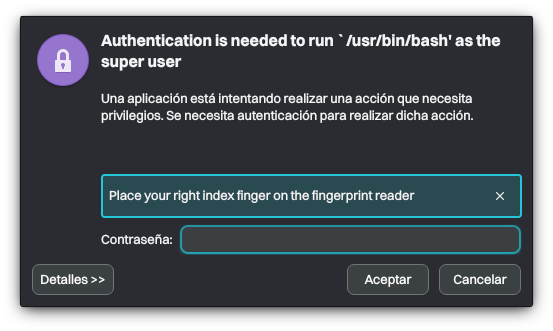
As mentioned, fingerprints can authenticate the user instead of the password for the Plasma lock screen, PolicyKit dialogs, and sudo.
- ⚠️ Important: Note that KWallet cannot be unlocked using a fingerprint reader.
That’s it; this concludes today’s tutorial.
